Cyberhaven Platform Overview
Cyberhaven is a data security platform that safeguards sensitive data from unauthorized access and unauthorized transfer outside the organization. It combines lightweight endpoint sensors, browser extensions, and connectors to deliver real‑time, granular visibility into how users interact with data. It tracks data lineage across network shares, SaaS applications, and endpoints to show where data came from, how it changed, and where it went. This enables protection based on classification and rapid investigations in the Console.
The platform delivers both Data Detection and Response (DDR) for data in motion and data in use, and Data Security Posture Management (DSPM) for data at rest discovery, classification, and catalog. DSPM is powered by forward and historical content scans via Connectors and surfaced in Discovery and the Data Catalog.
Features
-
Endpoint Sensors and browser extensions capture data‑in‑use and data‑in‑motion activity on monitored machines and browsers for precise lineage and enforcement.
-
Connectors extend lineage and discovery into SaaS and cloud services. They support forward and historical scans for content inspection and classification, and capture the metadata needed for correlation and analysis.
-
Classification covers data in motion, data in use, and data at rest using content scanning. Policies can then block, warn, or monitor based on sensitivity and context.
-
Console and dashboards present risks, events, incidents, lineage context, and trends.
-
Linea AI detects anomalous flows (even without predefined policies), assigns AI‑assessed risk and prioritization, and generates natural‑language incident summaries. Administrators can configure exclusions in Preferences → Linea AI Configuration.
Benefits
-
Strengthen protection with lineage‑aware detection and prevention guided by robust classification across data states.
-
Gain end‑to‑end visibility across endpoints, browsers, and cloud apps to understand use and movement of sensitive data.
-
Reduce investigation time with contextual lineage and intuitive views that summarize what happened and why it matters.
How it works
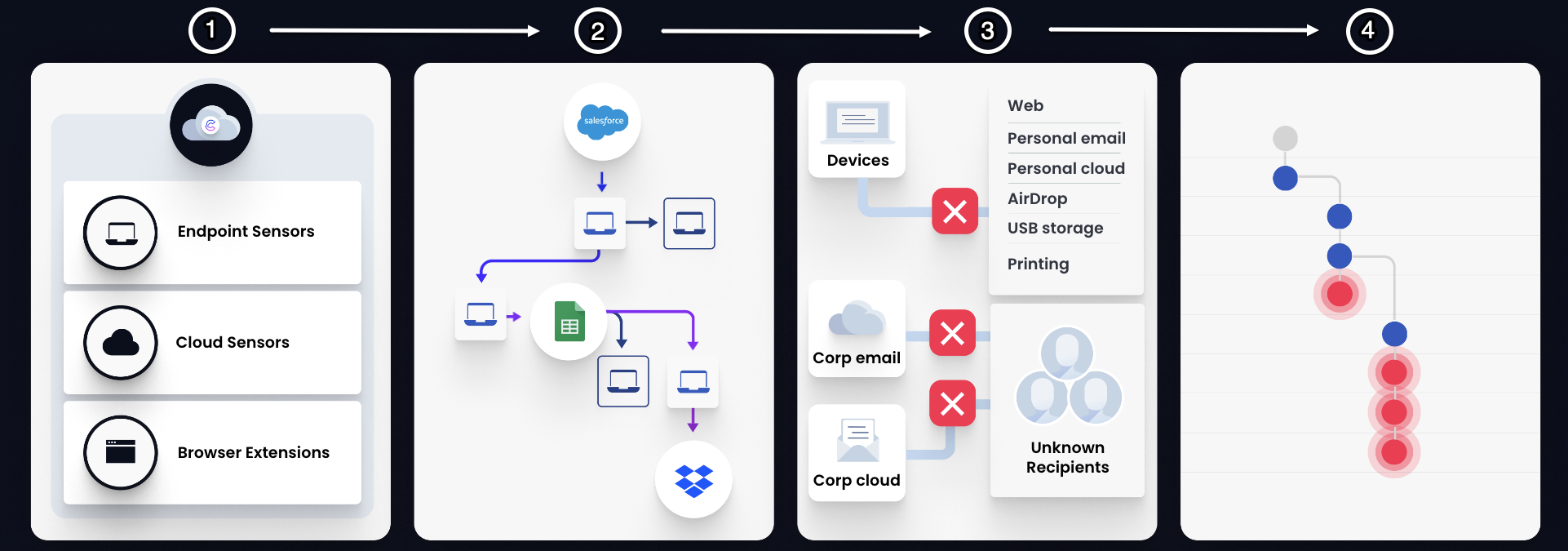
Cyberhaven correlates events from Endpoint Sensors and browser extensions with Connector events to reconstruct complete dataflows and lineage. Administrators define policies. The platform evaluates matching user actions at destinations against those policies and enforces the configured outcome (block, warn, or monitor) according to the policy conditions and the data’s sensitivity.
Architecture
At a high level, the platform delivers DDR and DSPM across three planes: collection (sensors, browser extensions, Connectors), analysis (classification, lineage construction, AI‑assisted risk assessment), and action (policy evaluation and enforcement, incident creation and summarization) surfaced in the Console for review and response. DSPM scan results are surfaced in Discovery and the Data Catalog; DDR events and incidents appear in Risks Overview and Incidents.
Core concepts
Data classification
Cyberhaven uses content scanning and context to classify data across all states.
-
Data in motion: Monitor movement between applications, cloud storage, and external devices. Record the source, destination, file path, and user for each transfer, including copies or transfers from machines with the Cyberhaven Sensor.
-
Data in use: Provide visibility into how users interact with data on monitored machines, browsers, and SaaS. Use this context to prevent unauthorized access to sensitive data.
-
Data at rest: Identify and classify data stored on machines where the Sensor is installed. Scan files and storage locations to determine content and sensitivity, then classify them against selected datasets. Scanning data at rest in advance allows immediate policy enforcement without waiting for data in motion or data in use events.
Read more: Content Inspection
Data lineage
Cyberhaven continuously tracks the history of data from its point of origin, monitoring movements and transformations so administrators can see destinations and how data changes over time.
Building data lineage
To build lineage, Cyberhaven identifies a file’s source and searches for prior events that match that source (e.g., locations, IDs, actors, timestamps), chaining related actions such as download → rename → compress → attempted upload.
Datasets
A dataset classifies data based on origin (e.g., source location, application, file type, content) and is a core input to policies used to block, warn, or monitor actions.
Policies
Policies define destination conditions for flows originating from datasets and determine the enforcement action when a match occurs (block, warn, monitor).
Policy enforcement
Sensors continuously monitor user actions and apply the first applicable blocking policy; if none apply, the first warning policy is enforced. Dataset matches are retained so newly created policies can be enforced promptly against previously observed data flows.
Example
A user downloads a corporate file, renames it, compresses it, and attempts to upload it to an external destination. Cyberhaven associates each step via shared location and metadata, creating a single lineage that shows origin, transformations, and attempted exfiltration for policy enforcement or investigation in the Console.